Domain Spoofing Mutiny, a Web-Based Bitcoin Wallet
In this article, I will address one potential danger of browser-based wallets called domain spoofing. More specifically, I want to use Mutiny to give a practical example of the risks of a specific type of domain spoofing called a homographic attack.

I believe that Mutiny Wallet is one of the most important projects in the Bitcoin space at the moment.
But why would a browser-based Bitcoin wallet be so significant?
Because one of the main value propositions of Bitcoin is its resistance to censorship. And paradoxically most wallets are hosted by app stores that are essentially walled gardens.
From time to time, we see apps suddenly being entirely removed from the App Store. Google and Apple can also force developers to remove certain features against the will of their users.
Damus being forced by Apple to remove the zap feature is the most recent example that comes to mind.
Once again, we have been reminded of the importance of maintaining non-censorable ways to access wallets.
Are you not so sure that the web is such a difficult platform to censor? Just remember that governments and corporations have been trying to shut down The Pirate Bay for almost 20 years without success.
Yeah, maintaining a wallet as a website on a browser makes it very hard to be stopped. But let us not forget that the decision to provide it on such platform comes at a cost.
In this article, I will address one potential danger of browser-based wallets called domain spoofing.
More specifically, I want to use Mutiny to give a practical example of the risks of a specific type of domain spoofing called a homographic attack.
https://en.wikipedia.org/wiki/IDN_homograph_attack
At the beginning of this research I wasn't certain of the seriousness of this issue. So, to make sure that this is something that we should talk about, I wanted to get my hands dirty and try to create the most misleading clone of Mutiny as possible.
The first step was to construct several fake domains by replacing some of the regular letters that compose 'mutinywallet' with greek, cyrillic and roman equivalents.
Here are some examples:
https://www.mυtinywallet.com

https://www.mutιnywallet.com
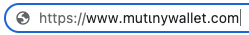
https://www.mutinүwallet.com
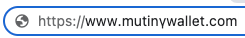
https://www.mutinywaḽḽet.com
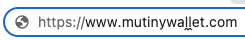
https://www.mutinywaʟʟet.com
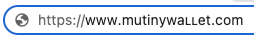
https://www.mutinywalleτ.com
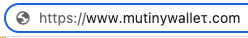
https://www.mutinywaḻḻet.com
This last one is actually my favorite, because a user may perceive the ḻḻ as underlines, and interpret it as a browser glitch. So i decided to move forward with this one.
The next step was to find out a domain registrar that supports Internationalized Domain Names. I picked Namecheap, because $20.93 felt like a bargain for domain, hosting and SSL certificate in the first year.
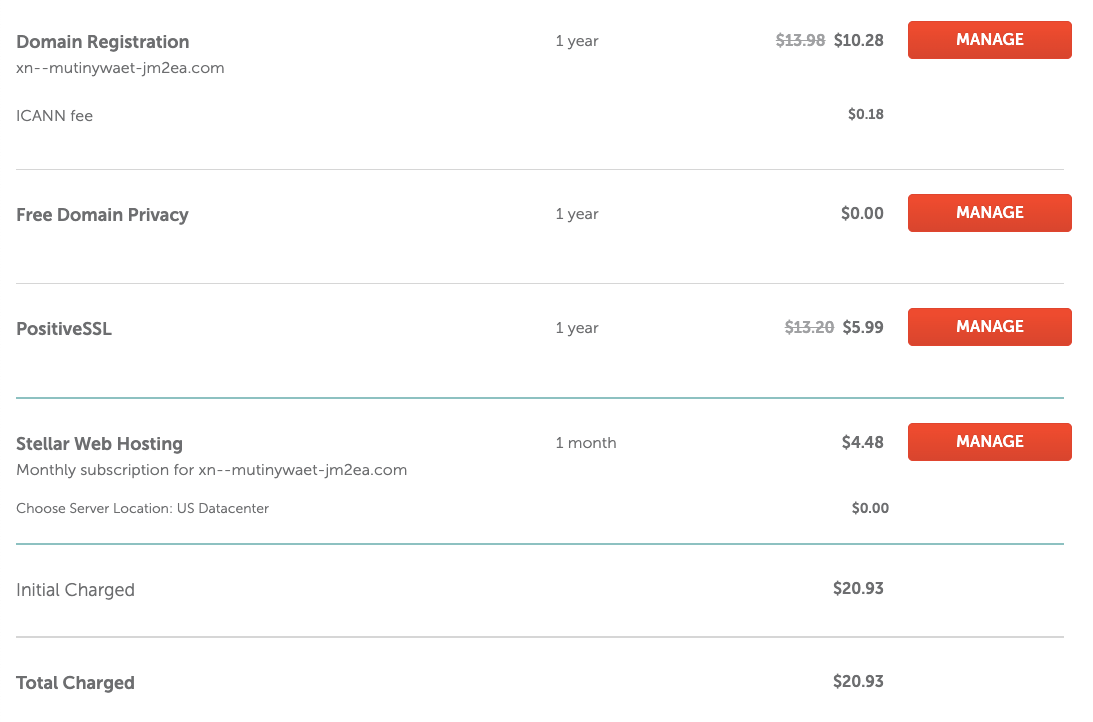
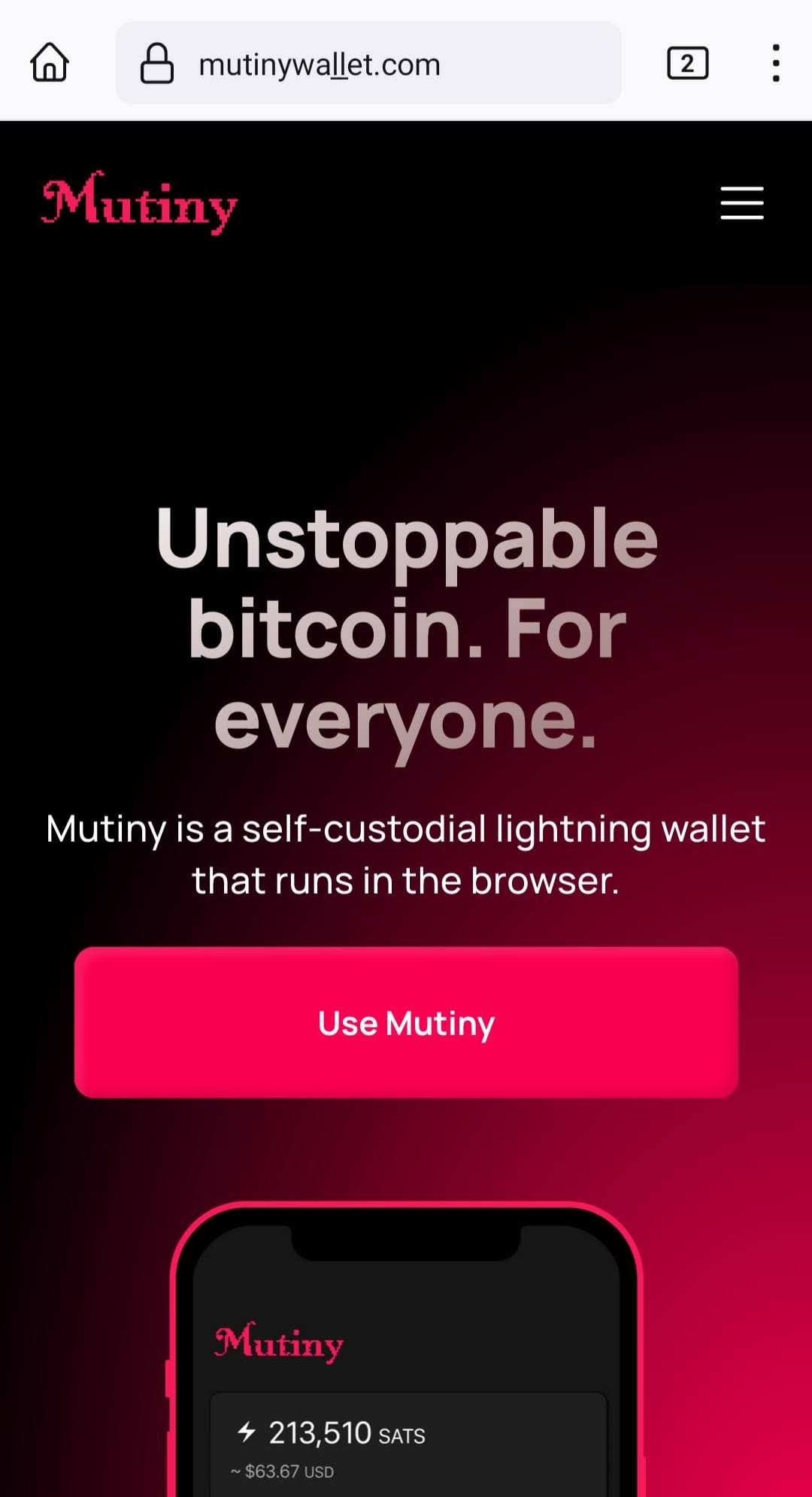
After installing the SSL certificate, I just copied the original Mutiny Wallet home page using a website cloner and uploaded it to the created hosting account.
There you go! You can now test the fake site yourself:
IMPORTANT: Depending on the browser that you are using, you may have a totally different experience, as you can see here:
Chrome (Desktop)
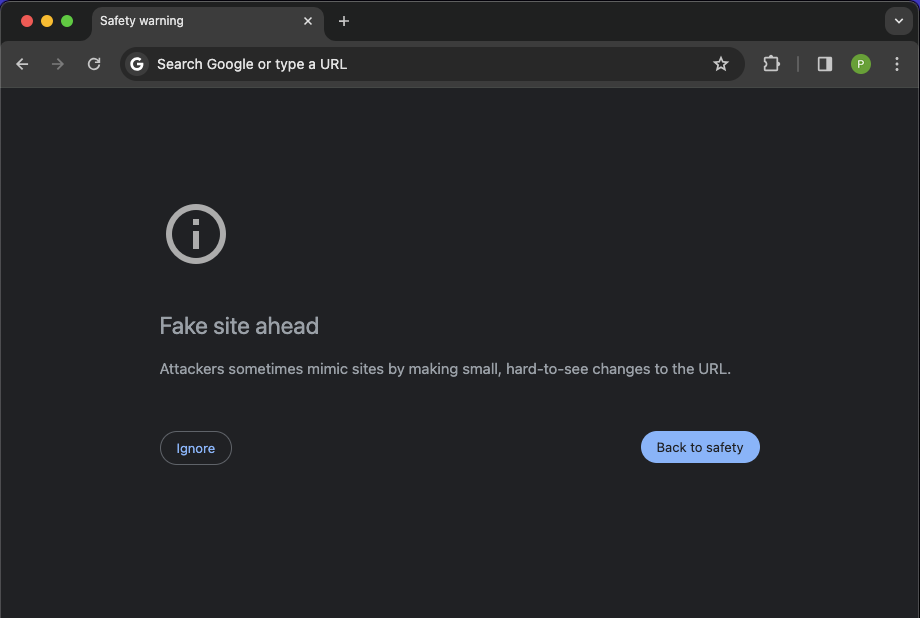
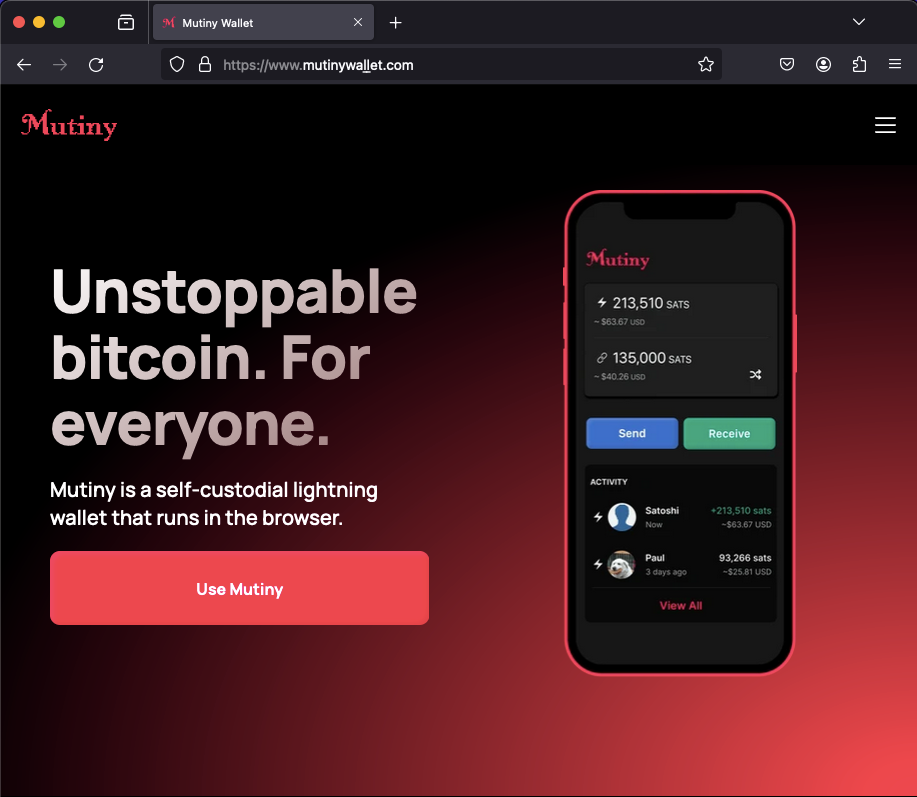
Safari (Desktop)
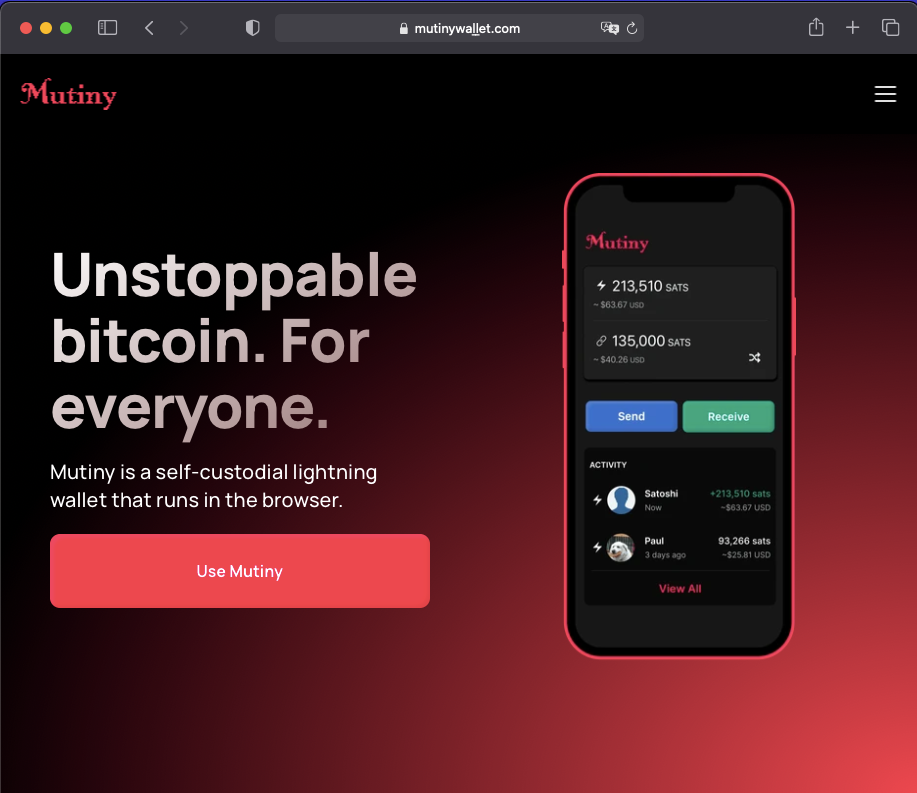
Firefox (Desktop)
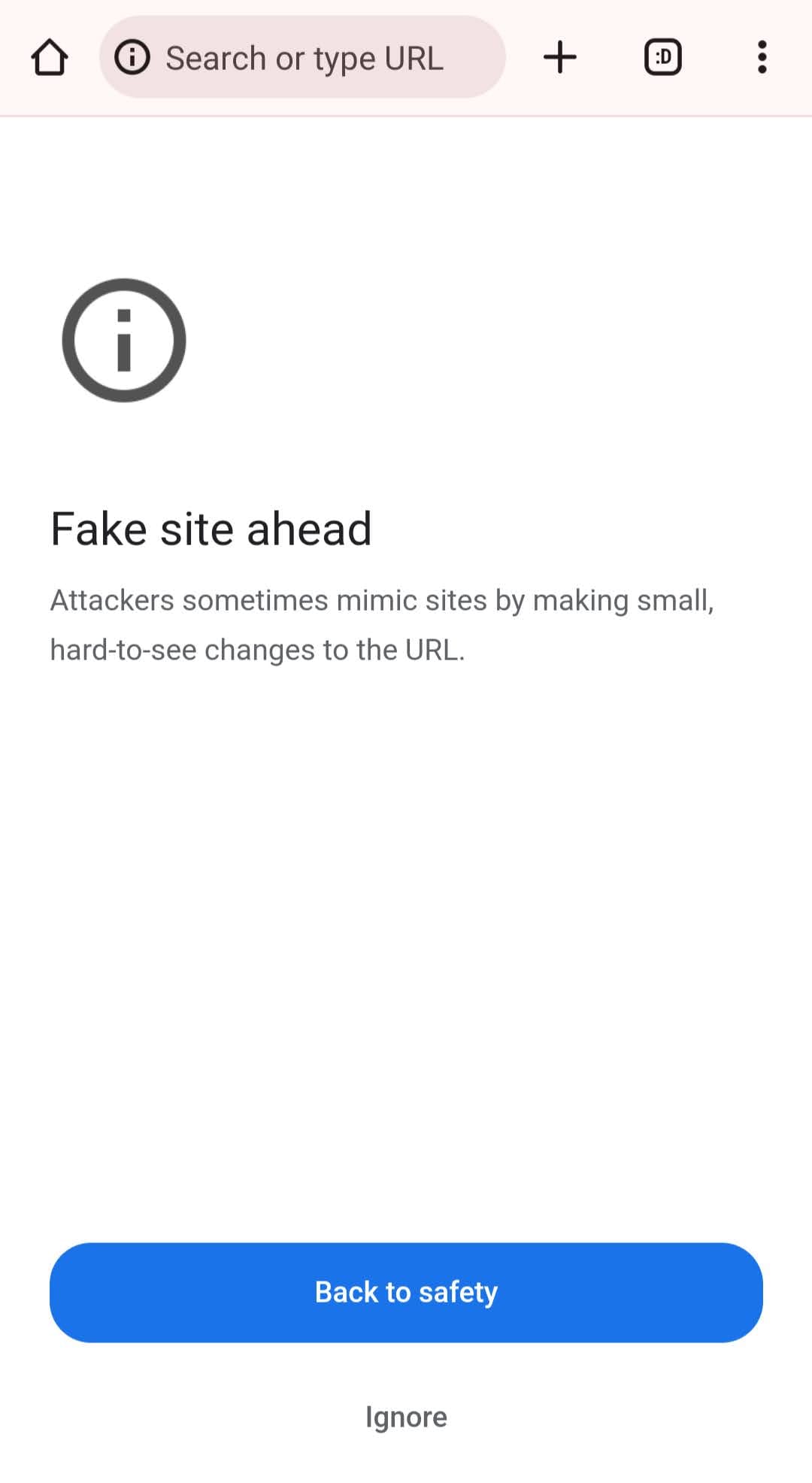
I shouldn't forget to mention that I had similar results when testing on mobile devices.
Chrome (Mobile)
Safari (Mobile)
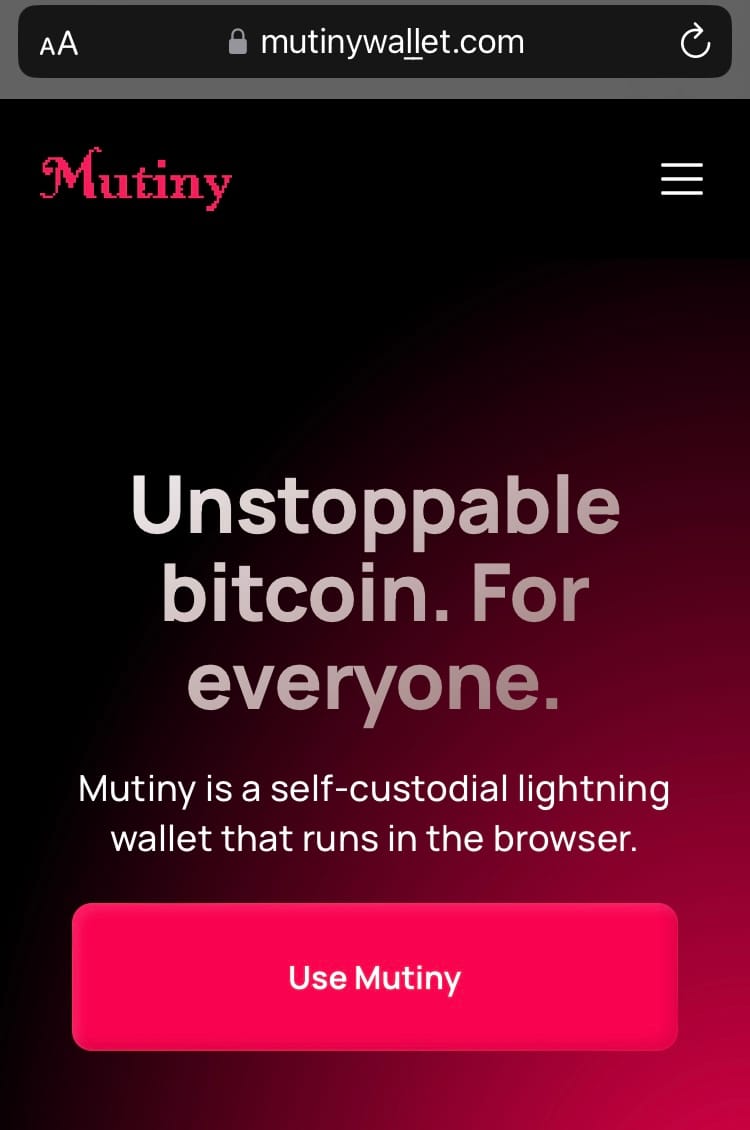
Firefox (Mobile)
Further insights
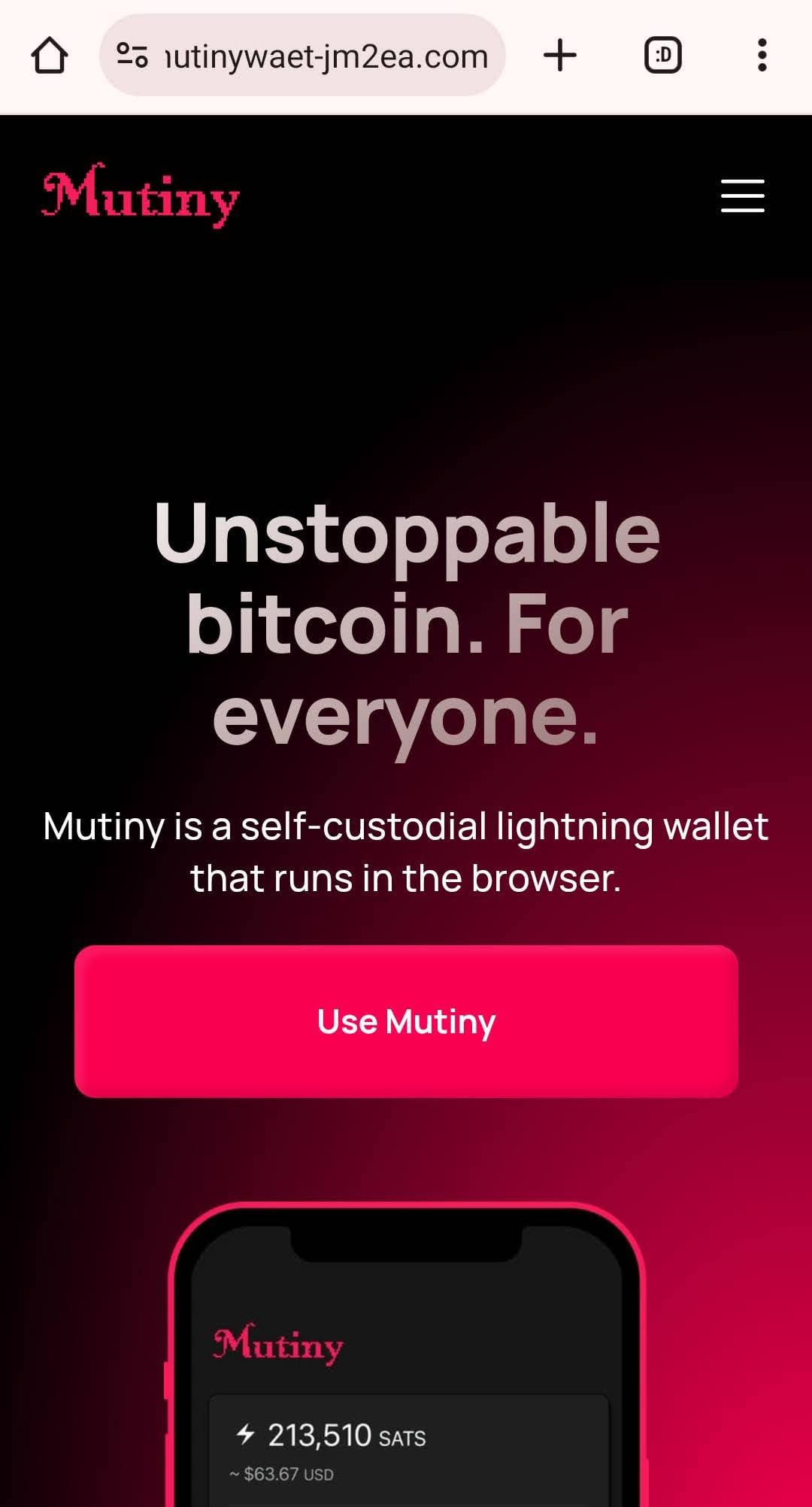
When the user decides to ignore the warning and go on (by clicking/tapping 'Ignore'), Chrome converts automatically the entered (fake) URL to its Punycode representation in the address bar: www.xn--mutinywaet-jm2ea.com
This is an extra security feature that can make a huge difference. And yes, I know, Punycode itself can also be used for phishing, but let's stay with classic spoofing. The conversion from the entered URL (with special charachters) to Punycode in the address bar didn't happen at all with Safari and Firefox.
Padlock icon on address bar
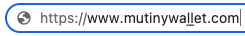
One troubling detail is that the padlock icon in the address bar can give the user a false sense of protection. The $5.99 I paid for the SSL certificate made a difference in terms of potentially misleading the user.
In this regard, Chrome is the real winner, as it was the only browser that did not display the padlock icon near the URL in the address bar, as you can see below:
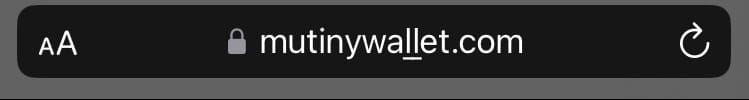
Yeah, I am happy to see that most users would be protected against this threat, as Chrome is the most used browser in the world.
But let's imagine for a minute what could happen if an attacker launched a Google or Facebook ad campaign specifically targeting users using the other two vulnerable browsers (Firefox and Safari)... A lot of seed phrases could be stolen from users trying to recover their wallets.
I hope this article will raise awareness of this issue and help people keep their funds safe.
So, let's finish with the one rule that protects users of a web-based bitcoin wallet:
Additionally, if you are using it on your smartphone, it may be a good idea to install it as a PWA. In other words, you will always have it on your home screen, just like a regular app. This can help you make sure that you are accessing the real thing.
